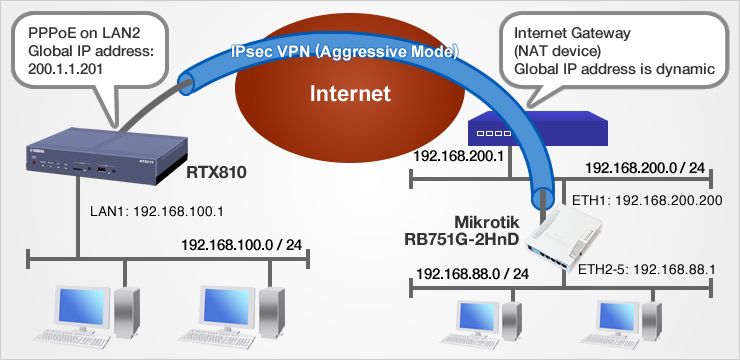
IPsec VPN (Aggressive) interconnection with MikroTik
IPsec setting example on RTX810 & MikroTik RB751G
| Parameter | Yamaha RTX810 | MikroTik RB751G-2HnD |
|---|---|---|
| Encryption algorithm | 3DES | 3DES |
| Hash algorithm | SHA1 | SHA1 |
| Authentication method | Pre-shared-key | Pre-shared-key |
| DH group | 2 (1024bit) | 2 (1024bit) |
| Local ID | - | “mikrotik” |
| Remote ID | “mikrotik” | - |
| Mode | Aggressive | Aggressive |
| Parameter | Yamaha RTX810 | MikroTik RB751G-2HnD |
|---|---|---|
| Peer | - | 200.1.1.201 |
| Encryption algorithm | 3DES | 3DES |
| Hash algorithm | SHA1 | SHA1 |
| Local ID | 192.168.100.0/24 | 192.168.88.0/24 |
| Remote ID | 192.168.88.0/24 | 192.168.100.0/24 |
| Mode | Quick | Quick |
VPN configuration setting with IPsec
| LAN interface settings (Use LAN1 Interface) |
ip lan1 address 192.168.100.1/24 |
|---|---|
| WAN Interface settings (Use LAN2 Interface) |
pp select 1 |
| pp keepalive interval 30 retry-interval=30 count=12 | |
| pp always-on on | |
| pppoe use lan2 | |
| pppoe auto disconnect off | |
| pp auth accept pap chap | |
| pp auth myname (User ID) (Password) | |
| ppp lcp mru on 1454 | |
| ppp ipcp ipaddress on | |
| ppp ipcp msext on | |
| ppp ccp type none | |
| ip pp nat descriptor 1000 | |
| pp enable 1 | |
| ip route default gateway pp 1 | |
| NAT settings | nat descriptor type 1000 masquerade |
| nat descriptor masquerade static 1000 1 192.168.100.1 udp 500 | |
| nat descriptor masquerade static 1000 2 192.168.100.1 esp | |
| nat descriptor masquerade static 1000 3 192.168.100.1 udp 4500 | |
| DHCP Server settings | dhcp service server |
| dhcp server rfc2131 compliant except remain-silent | |
| dhcp scope 1 192.168.100.2-192.168.100.191/24 | |
| DNS settings | dns server pp 1 |
| dns private address spoof on | |
| IPsec VPN settings | tunnel select 1 |
| ipsec tunnel 1 | |
| ipsec sa policy 1 1 esp 3des-cbc sha-hmac local-id=192.168.100.0/24 remote-id=192.168.88.0/24 | |
| ipsec ike keepalive log 1 on | |
| ipsec ike keepalive use 1 on dpd | |
| ipsec ike local address 1 192.168.100.1 | |
| ipsec ike local id 1 192.168.100.0/24 | |
| ipsec ike nat-traversal 1 on | |
| ipsec ike payload type 1 3 | |
| ipsec ike pre-shared-key 1 text (Pre-shared-key) | |
| ipsec ike remote address 1 any | |
| ipsec ike remote id 1 192.168.88.0/24 | |
| ipsec ike remote name 1 mikrotik key-id | |
| ip tunnel tcp mss limit auto | |
| tunnel enable 1 | |
| ipsec auto refresh on | |
| ip route 192.168.88.0/24 gateway tunnel 1 | |
| Filter settings | ip filter 200000 reject 10.0.0.0/8 * * * * |
| ip filter 200001 reject 172.16.0.0/12 * * * * | |
| ip filter 200002 reject 192.168.0.0/16 * * * * | |
| ip filter 200003 reject 192.168.100.0/24 * * * * | |
| ip filter 200010 reject * 10.0.0.0/8 * * * | |
| ip filter 200011 reject * 172.16.0.0/12 * * * | |
| ip filter 200012 reject * 192.168.0.0/16 * * * | |
| ip filter 200013 reject * 192.168.100.0/24 * * * | |
| ip filter 200020 reject * * udp,tcp 135 * | |
| ip filter 200021 reject * * udp,tcp * 135 | |
| ip filter 200022 reject * * udp,tcp netbios_ns-netbios_ssn * | |
| ip filter 200023 reject * * udp,tcp * netbios_ns-netbios_ssn | |
| ip filter 200024 reject * * udp,tcp 445 * | |
| ip filter 200025 reject * * udp,tcp * 445 | |
| ip filter 200026 restrict * * tcpfin * www,21,nntp | |
| ip filter 200027 restrict * * tcprst * www,21,nntp | |
| ip filter 200030 pass * 192.168.100.0/24 icmp * * | |
| ip filter 200031 pass * 192.168.100.0/24 established * * | |
| ip filter 200032 pass * 192.168.100.0/24 tcp * ident | |
| ip filter 200033 pass * 192.168.100.0/24 tcp ftpdata * | |
| ip filter 200034 pass * 192.168.100.0/24 tcp,udp * domain | |
| ip filter 200035 pass * 192.168.100.0/24 udp domain * | |
| ip filter 200036 pass * 192.168.100.0/24 udp * ntp | |
| ip filter 200037 pass * 192.168.100.0/24 udp ntp * | |
| ip filter 200080 pass * 192.168.100.1 udp * 500 | |
| ip filter 200081 pass * 192.168.100.1 esp * * | |
| ip filter 200082 pass * 192.168.100.1 udp * 4500 | |
| ip filter 200098 reject-nolog * * established | |
| ip filter 200099 pass * * * * * | |
| ip filter 500000 restrict * * * * * | |
| ip filter dynamic 200080 * * ftp | |
| ip filter dynamic 200081 * * domain | |
| ip filter dynamic 200082 * * www | |
| ip filter dynamic 200083 * * smtp | |
| ip filter dynamic 200084 * * pop3 | |
| ip filter dynamic 200085 * * submission | |
| ip filter dynamic 200098 * * tcp | |
| ip filter dynamic 200099 * * udp | |
| pp select 1 | |
| ip pp secure filter in 200003 200020 200021 200022 200023 200024 200025 200030 200032 200080 200081 200082 | |
| ip pp secure filter out 200013 200020 200021 200022 200023 200024 200025 200026 200027 200099 dynamic 200080 200081 200082 200083 200084 200085 200098 200099 | |
| pp enable 1 |
Required Setting on MikroTik Winbox
Set the followings from initial configuration.
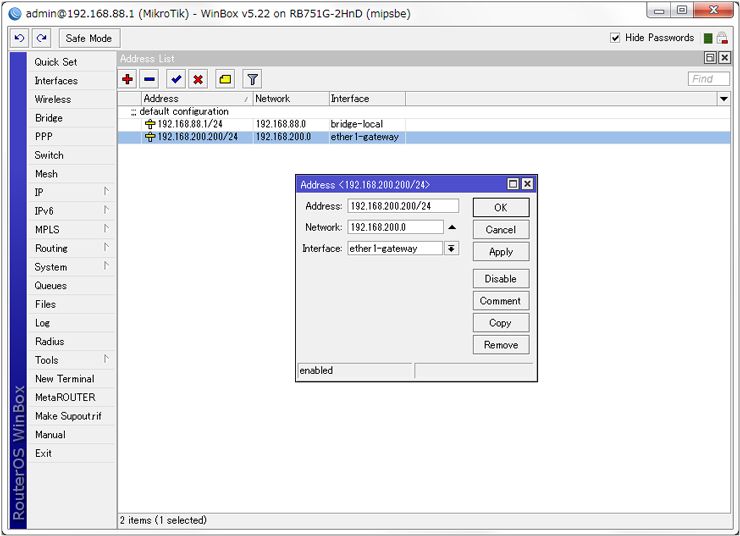
Interface address setting
Location: [IP] – [Addresses]
Configure interface address setting.
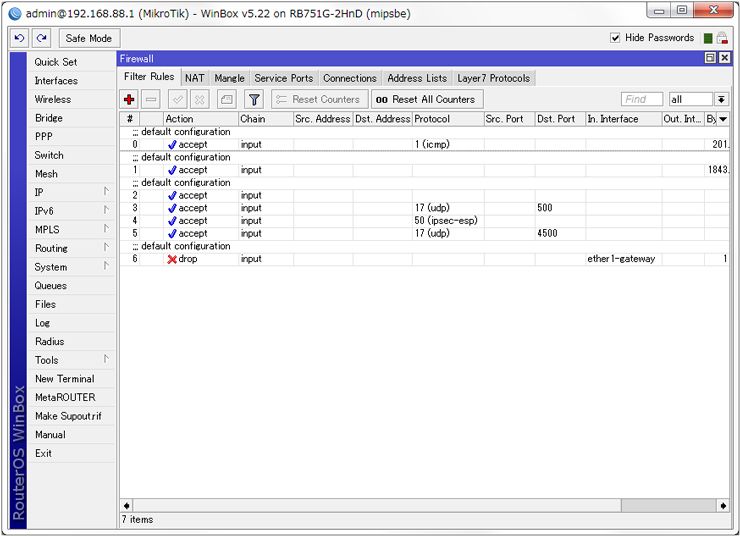
Firewall setting
Location: [IP] – [Firewall] – [Filter Rules]
Add input filter for UDP destination port 500 (IKE).
Add input filter for ipsec-esp (ESP).
Add input filter for UDP destination port 4500 (NAT Traversal)
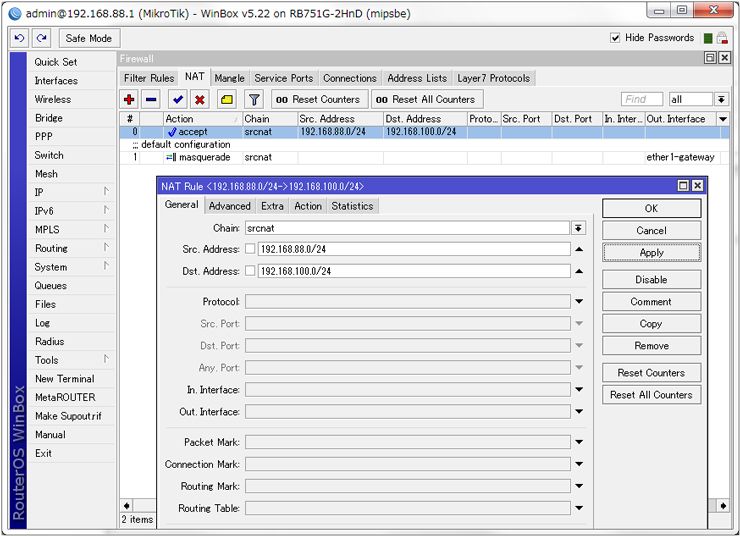
NAT setting
Location: [IP] – [Firewall] – [NAT]
Add NAT entry for communication to opposite site.
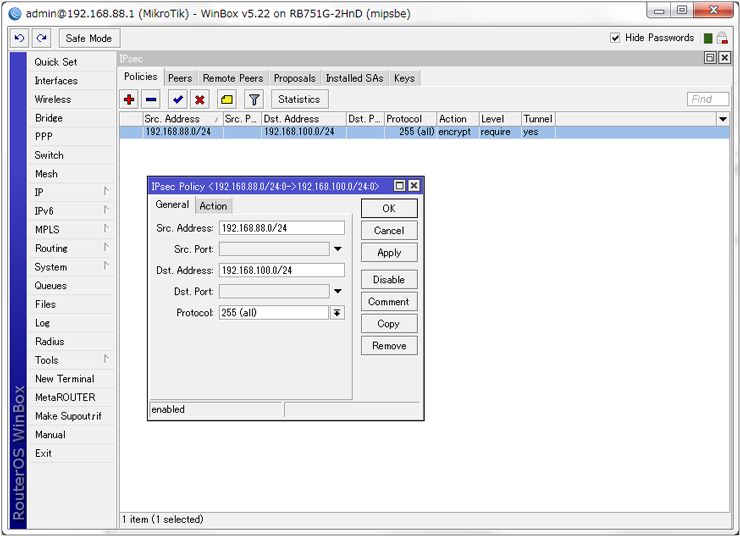
IPsec Policies setting
Location: [IP] – [IPsec] – [Policies]
Add IPsec Policies.
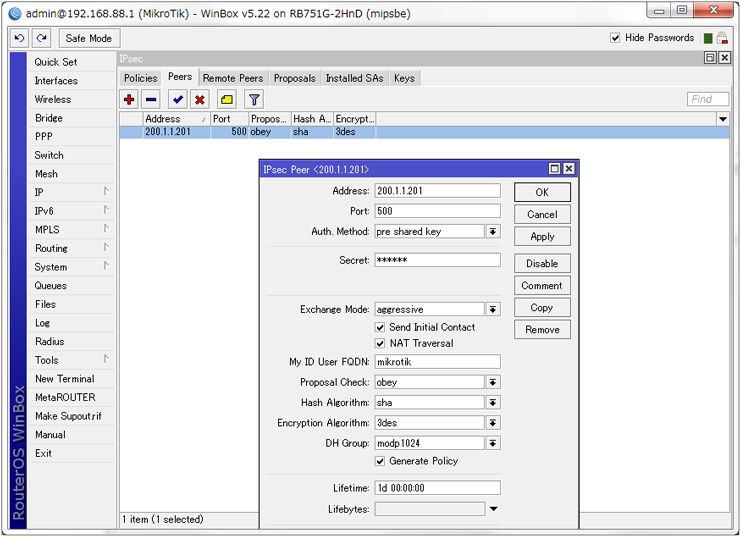
IPsec Peers setting
Location: [IP] – [IPsec] – [Peers]
Add IPsec Peers.
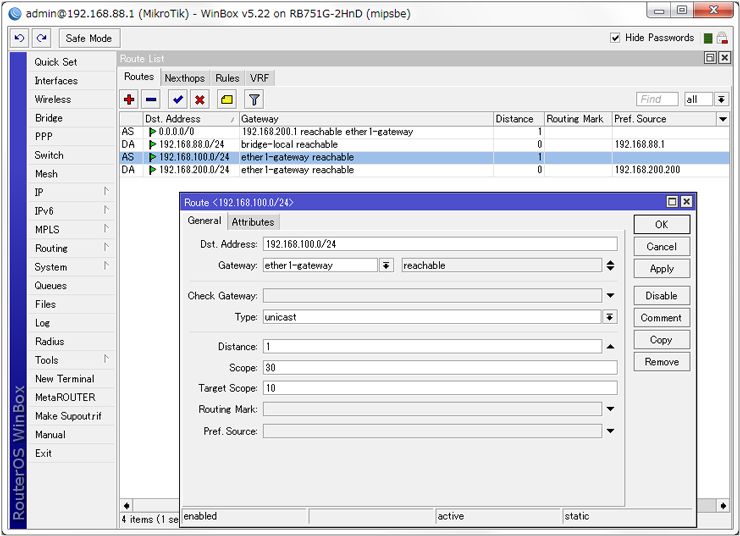
Route setting
Location: [IP] – [Routes] – [Routes]
Add Route setting to opposite site.